True Story: The Case Of A Hacked Baby Monitor (Gwelltimes P2P Cloud)
IoT news vulnerability
How it all started
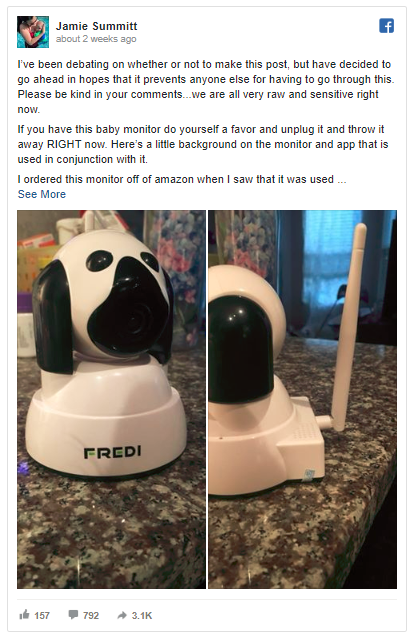
Earlier this month, news articles surfaced (Daily Mail, ABC News, NPR) on a case where a mother from South Carolina USA, Jamie Summitt, claims that her baby monitor was hacked and used to spy on her and her baby. The SEC Consult Vulnerability lab has already published issues with baby monitors in the past, so this case struck our interest. We decided to dig a bit into the technical details of the case.
What we know
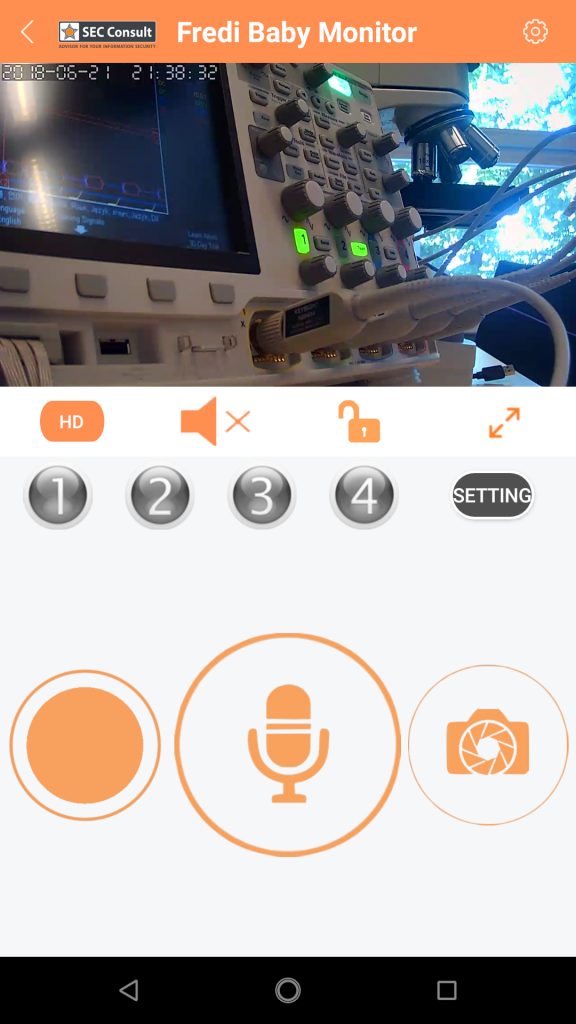
The device is branded as “FREDI” and is offered via Amazon.com, Amazon.de et al. There is a vendor website at www.fredicctv.com. According to the product description the device is a 360-degree IP camera with infrared night vision, that has a built-in microphone and speaker and connects via Wi-Fi. iOS and Android apps for remotely connecting to the device, are available. The product description refers to FRP2P (10.000+ installs, recently removed from the Play Store!) and YYP2P (1.000.000+ installs), but apps like Yoosee (1.000.000+ installs) and Sricam (500.000+ installs) are mentioned as well.
The woman from the Facebook post claims that someone controlled the camera remotely and spied on her, possibly listened in to conversations etc., basically all things that are within the outlined functionality of the camera and apps.
Supply chain
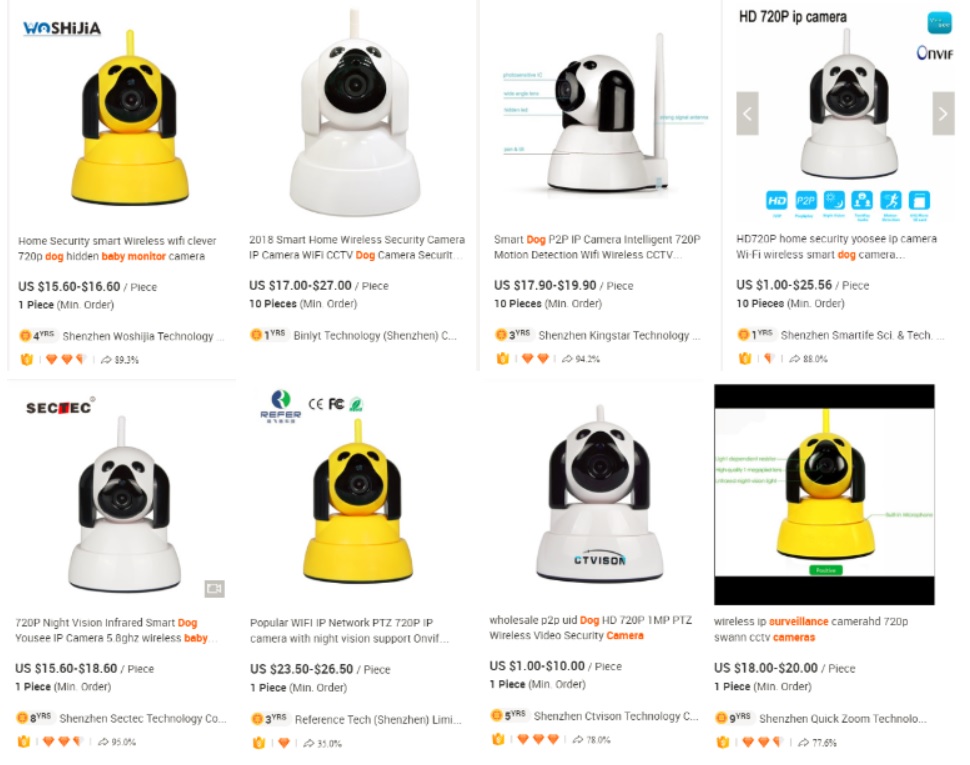
A quick search on Alibaba.com (a B2B platform for importers and exporters) reveals that there are several suppliers for this type of camera (e.g. search for “dog surveillance camers”, “dog baby monitor”):
Most of them offer “OEM/ODM” services for wholesale customers that include custom branding. For example, “Shenzhen Ctvison Technology Co., Ltd.” offers customization starting with a logo (“high resolution logo in JPG format”), labeling (“please offer us your own model numbers”) , creation of a user manual (“Please offer us the finished manual file”) and even custom package design.
Do you want to start out in the dog-shaped surveillance camera or baby monitor business? Just invent your own brand and place your order. That’s probably what the company behind the “FREDI” brand did.
But who is actually manufacturing these devices? More on that later.
Attack surfface
Local Network
- TCP Port 554: RTSP, provides access to the video stream, no authentication required (URLs for use in video players, e.g. VLC: high resolution: rtsp://IP:554/onvif1, low resolution: rtsp://IP:554/onvif2)
- TCP Port 5000: ONVIF, only some functionality implemented, no authentication required
The device does not support UPnP, so it is unlikely that the device configured port forwarding for these ports. Unless the ports are explicitly exposed by the user (unlikely), an attacker would need access to the local network to connect to these ports.
“P2P Cloud”
Like most consumer grade surveillance products this device has a “P2P cloud” feature that is enabled by default. The device connects to a cloud server infrastructure and keeps this connection up. All supported smartphone and desktop apps can connect to the device via the cloud. From a usability perspective this makes it easier for users to interact with the product, since the user does not have to be in the same network (e.g. the same Wi-Fi network) to be able to connect to the device. Additionally, no firewall rules, port forwarding rules or DDNS setup are required on the router.
However, this approach has several security implications:
- The cloud server provider gets all the data (e.g. video streams that are viewed).
- Open questions: Who runs these servers? Where are they located? Do they comply with local jurisdiction, e.g. also EU GDPR?
- If the data connection is not properly encrypted, anyone who can intercept the connection is able to monitor all data that is exchanged.
- The “P2P Cloud” feature bypasses firewalls and effectively allows remote connections into private networks. Now attackers can not only attack devices that have been intentionally/unintentionally exposed to the web (classic “Shodan hacking” or the Mirai approach) but a large number of devices that are exposed via the “P2P Cloud”.
So how does this “P2P Cloud” feature work in practice? On the back of the device there is an ID Code and a password (ID: 11610289, password: 123). In the supported app (e.g. YYP2P) there is an “Add online device” function that allows you to add the device. Unfortunately the device ID does not look very secure. Plus the default password is neither randomly generated nor device-specific. Unless the user has changed the password to a secure one, anyone can log in and interact with the camera by “trying” different cloud IDs.

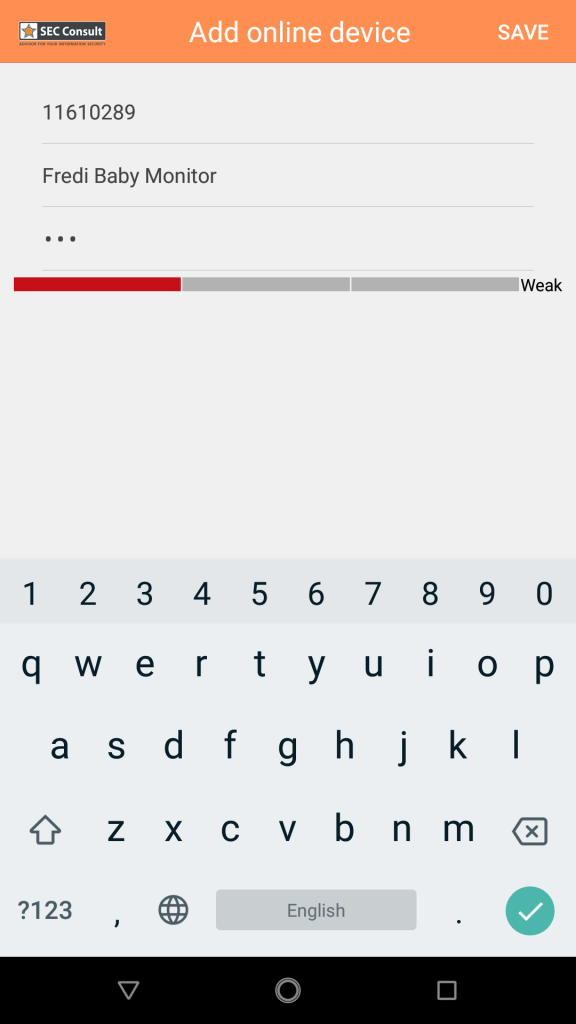
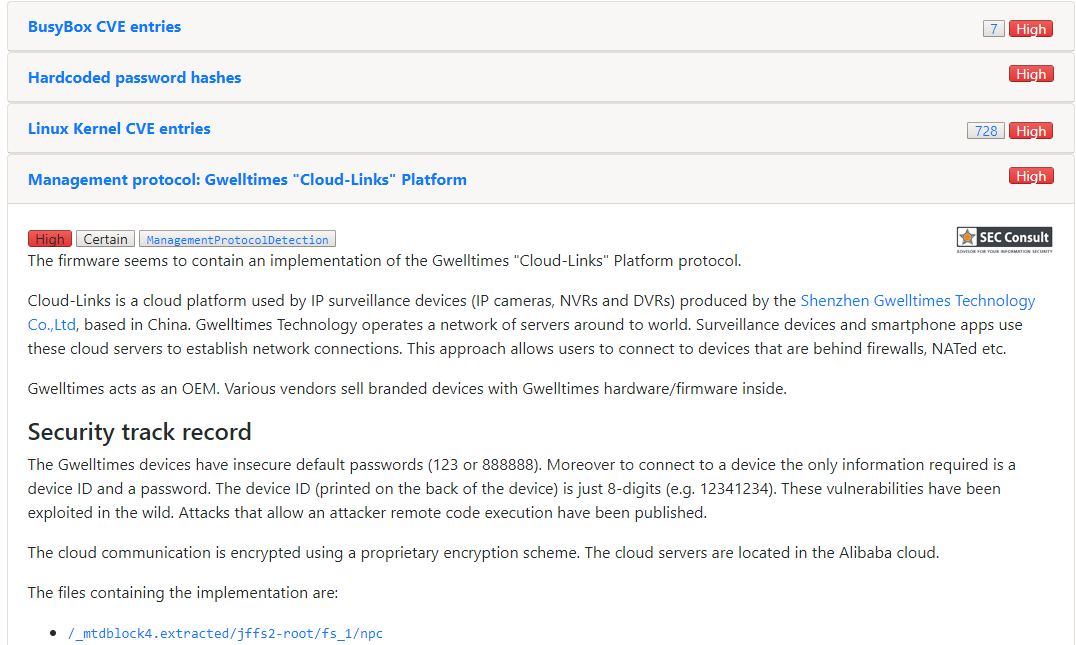
Interestingly, Berlin-based Security Research Labs has published research on the “P2P Cloud” also used by this camera (Blog Post, DeepSec Vienna 2017 “Next-Gen Mirai” Slides) in November 2017. They presented a full attack that starts with scanning for valid device IDs, brute forcing passwords and then exploiting missing firmware update integrity/authenticity checks to gain remote code execution and persistence on the device. Be sure to check it out! They reported the issues. Apparently they have not been fixed.
Shenzhen Gwelltimes Technology Co., Ltd.
So who is responsible for this mess? Everything points to a China-based company called Shenzhen Gwelltimes Technology Co., Ltd. This company is an OEM that develops the camera firmware, designs the hardware and operates the cloud service. They likely have the same business model as Hangzhou Xiongmai Technology Co.,Ltd., another China-based company that gained questionable fame as a big portion of the “Mirai” botnet were Xiongmai devices.
Gwelltimes offer a “generic” mobile app called Yoosee (1.000.000+ installs), a Windows client CMSClient) and an SDK for iOS and Android that allows anyone to create custom, branded apps (more information: Github sample project).
Final Thoughts
In the South Carolina case the most likely scenario is that someone is scanning for valid device IDs with insecure/default passwords and then spies on the owners of the device, possibly based on the information released by Security Research Labs in November 2017.
Obviously, the device and the cloud service is not GDPR compliant. Here we have a Chinese company that is never mentioned anywhere, developing insecure products and sending our most private information home to their Chinese servers. Although they have been confronted with the security issues months ago, they have decided not to fix them.
It seems that consumer electronics with opaque supply chains, paired with insecure, built-in cloud features that are enabled by default will keep us busy in the future.
The firmware security analysis platform IoT Inspector detects dangerous P2P cloud functionality in the firmware of IoT devices, including the Gwelltimes Cloud-Links Platform. The firmware of the FREDI device is available as part of our IoT Inspector Demo. Interested? Register online at www.iot-inspector.com to get a demo.
Addendum: Hardware Hacking
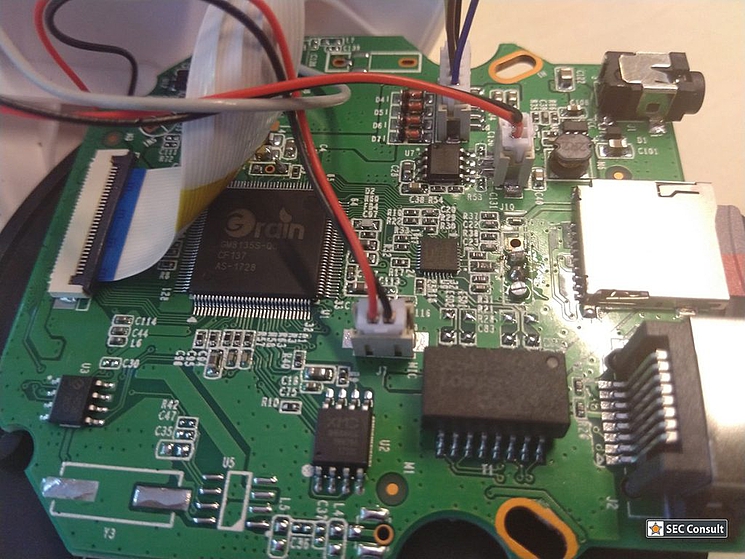
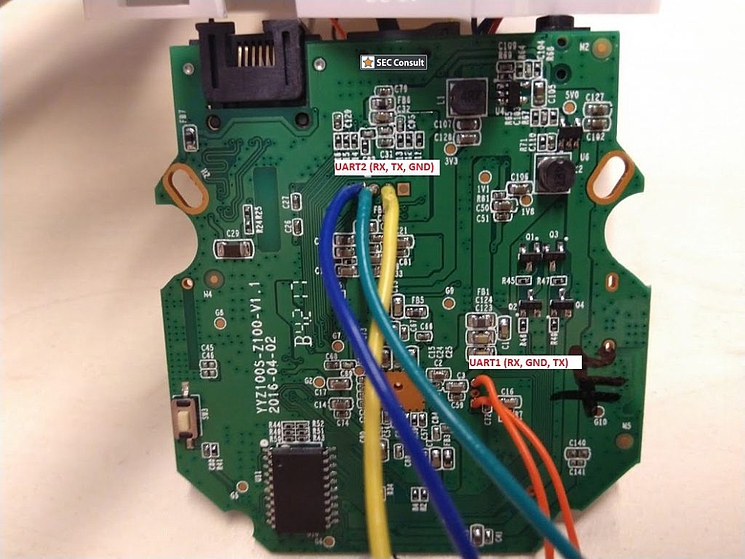
For the sake of completeness, SEC Consult also had a short look at the hardware as well. The SoC is a Grain Media GM8135S-QC (product brief). We found a nice data sheet for the chip on a Russian site, which also includes the schematics of the chip. There are two UART interfaces available with UART1 dropping you right into a root shell. A good starting point for doing further analysis of the device and the cloud protocol.
Photos of the board, UART location and chip pinout:
Addendum: “indicators Of Compromise”
Want to hunt for devices using the Gwelltimes “Cloud-Links” platform in your infrastructure? Here are some domains/IPs used by the platform:
p2p1.cloudlinks.cn
p2p4.cloud-links.net
p2p2.cloudlinks.cn
p2p3.cloud-links.net
p2p5.cloudlinks.cn
p2p6.cloudlinks.cn
p2p7.cloudlinks.cn
p2p8.cloudlinks.cn
p2p9.cloudlinks.cn
p2p10.cloudlinks.cn
api1.cloudlinks.cn
api2.cloudlinks.cn
api3.cloud-links.net
api4.cloud-links.net
6sci.com
6sci.com.cn
videoipcamera.cn
videoipcamera.com
ht.hnhyws.com
www.hblottery.org
www.hbticai.org
www.zxicloud.com
camnoopy.cn
gxyaj.cn
220.231.128.12
121.43.181.184
123.206.9.74
47.91.77.247
49.51.39.15
54.255.195.121
This research was done by Stefan Viehböck (@sviehb) and “Hardware Hacking” done by Thomas Weber on behalf of SEC Consult Vulnerability Lab.