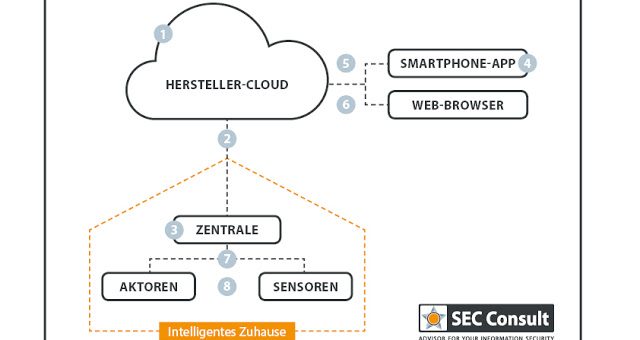
They aim to make our life easier with fancy functions like controlling your heating system with your tablet or switching your alarm system on and off with just a fingertip. But it must also be considered, that these new systems bring along new threats. And since these systems directly connect the virtual world with our real life, the threats could have a real big impact.Most of the security related smart home research focuses on the local communication area of smart home systems, where all the smart home devices communicate with the central base station. While in this area a lot of security shortcomings [2] [3] [4] [5] have already been identified by researchers, it is very important to also analyze the web area of smart home systems, where people communicate with the central smart home base station via their smartphone or web browser. As SEC Consult already showed in recent advisories, it is possible to take over control of a specific smart home system, simply by exploiting traditional web vulnerabilities and design flaws [6] [7]. Therefore, experts of the SEC Consult vulnerability lab examined this area for some other vendors in the scope of a limited security crash-test. This was done in cooperation with the leading German business newspaper WirtschaftsWoche.
Six products were tested in the context of this crash-test. Three of them, Gigaset Elements, RWE Smart Home und Qivicon, had already been tested before by WirtschaftsWoche in cooperation with AV-Test [8]. These products performed very well in the course of our crash-test. This indicates, that regular security audits really increase the level of application security. The new product of eQ-3, Homematic IP, also performed very well. While the previous product line had to deal with several weaknesses [4], the new product looks good at least at the perspective of a short crash-test within the web functionality.
Multiple vulnerabilities have been identified for the smart home solution of Digitalstrom. Traditional Cross-Site Scripting and Cross-Site Request Forgery attacks could be used to control arbitrary devices connected to the smart home system [9]. A further weakness was identified within the smartphone app of Devolo Home Control, which stores user credentials in plaintext on the phone. If the smartphone gets lost or stolen, the attacker can be able to steal the credentials and take over control of the system. [11]
Although the local communication area wasn’t in the scope of the conducted crash-test, it has to be mentioned that at least the protocols used by Digitalstrom and Devolo are not sufficiently protected. Digitalstrom’s communication is powerline based and according to the vendor it is unencrypted [12]. Its protection is completely dependent on physical isolation. Besides their own powerline protocol, Devolo also supports the radio-based protocol Z-Wave. The built-in Z-Wave chip of the tested room thermostat is an old model from the series 300 (ZW0301), which has no security features built-in. [13]
At a lower level, where it comes to firmware extraction, big differences between the vendors have been observed. The firmware forms the link between the software and the hardware of a device. It is very easy to extract the firmware of RWE devices. While other vendors at least make the hacker’s life a bit harder, it’s still possible with reasonable effort. Only Homematic IP devices implement different hardware-based security mechanisms.
After the extraction of a device’s firmware, it is possible to test it for further vulnerabilities. In the course of a quick check the usage of outdated software was identified for Gigaset, RWE and Devolo. Furthermore, there are publicly known vulnerabilities available for some of these outdated components. Although these vulnerabilities aren’t exploitable under the current circumstances, e.g. a certain change in the firmware-configuration would be sufficient to make the device of Devolo vulnerable to serious attacks. The basic problem here is the vendor’s insufficient security analysis of third party components. The firmware’s basis is bought from a third party but their security isn’t verified sufficiently.
Based on the conducted tests it is obvious that most of the vendors already raised their security level based on previous systematic security audits. However, if these audits are insufficient or missing, critical smart home systems still contain old and traditional web vulnerabilities.
This big difference in the security level of different smart home products is not visible for end-consumers, it could just be revealed by professional security audits. However, the question remains why vendors don’t invest in security audits sufficiently before they launch their products. The German interior minister Thomas de Maizière is already thinking about product liability and compensation regarding the digital carelessness of vendors. [14]
To sum it up, it can be stated that traditional (web-) vulnerabilities in smart home systems aren’t a thing of the past, but are still a real threat in modern and critical smart home systems.
Sources
[1] D. Schwarz, “The Current State of Security in Smart Home Systems – Threats in the Internet of Things”, SEC Consult Vulnerability Lab, 2016
[2] B. Fouladi and S. Ghanoun, “Security Evaluation of the Z-Wave Wireless Protocol”, Black Hat USA, vol. 24, 2013.
[3] J. Cache, J. Wright, and V. Liu, “Hacking Exposed Wireless: Wireless Security Secrets & Solutions”, The McGraw-Hill Companies, 2010.
[4] Sathya and Malli, “Attacking HomeMatic”, CCC 30C3, 2013
[5] T. Zillner and S. Strobl, “ZigBee Exploited”, Blackhat USA, 2015
[6] SEC Consult Vulnerability Lab, “Loxone Smart Home – Multiple Vulnerabilities”, 2015
[7] SEC Consult Vulnerability Lab, “Loxone Smart Home – Multiple Vulnerabilities – Part 2”, 2015
[8] T. Kuhn, “Sicherheitsrisiko Smart Home – Die Hacker kommen durch den Kühlschrank”, WirtschaftsWoche, 2014
[9] SEC Consult Vulnerability Lab, “Multiple vulnerabilities in Digitalstrom Konfigurator”, 2016
[10] OWASP, “OWASP Top Ten Project”, 2013
[11] SEC Consult Vulnerability Lab, “Insecure credential storage in my devolo Android app”, 2016
[12] digitalSTROM AG, “FAQ”
[13] C. Gomez and J. Paradells, “Wireless home automation networks: A survey of architectures and technologies”, IEEE Communications Magazine, vol. 48, no. 6, pp. 92–101, June 2010
[14] S. Krempl, “IT-Gipfel: Produkthaftung gegen die ‘digitale Sorglosigkeit'”, heise online, 2015