Further information about these attacks is available at:
The high number of Ubiquiti Networks devices on the web is due to an insecure default configuration. Remote administration is enabled by default. Contrary to best practice this exposes the HTTP/HTTPS and SSH administration service to the web (via the WAN port). This issue has been discussed on the support forums on several occasions. The Ubiquiti Networks employees’ statements were:
“After we disabled management to WAN interface by default, there were many many complaints. Many WISPs still need access to the WAN interface for: provisioning the devices, and management — even when in place at customer’s home, the WISPs still want access.” – Ubiquiti Networks Support
“We did disable remote management by default, and took a lot of flack from our users, so we reverted it.” –Ubiquiti Networks Support
This “insecure out of the box” approach is unique among network device vendors. WISPs are Wireless Internet Providers, who offer broadband services using Ubiquiti Networks gear. Ars Technica has a feature on one of these WISPs.
Attackers can remotely exploit weak passwords and vulnerabilities in the firmware to gain access to affected devices and are doing just that right now. After gaining access to the device, attackers can create a large botnet that can be used for DDoS attacks, spamming etc. The affected device class is a valuable target as it not only allows access to the internal network but also access to traffic that passes through it. Attackers can redirect DNS queries (e.g. to attack online banking sites) or even infect web downloads by people who connect to the internet via the device.
As organizations and individuals struggle with securing embedded devices, a long lifespan of an infection is guaranteed.
Another vulnerability lies in the reuse of cryptographic secrets. A certificate including its private key is embedded in the firmware of several Ubiquiti Networks products. This certificate is used for the HTTPS service (default server certificate for web based management) and is the same on all devices. An attacker in a privileged network position can execute man-in-the-middle or passive decryption attacks on the HTTPS communication. These attacks allow access to sensitive information like admin credentials. This vulnerability is significantly harder to exploit than the vulnerability discussed above. However, searching for the certificate fingerprint in data from internet-wide scans is a low-cost way of finding the IPs of specific products/product groups and allows us to measure how many Ubiquiti Networks devices are exposed to the web.
The Scans.io project by University of Michigan and Rapid7 periodically scans the public internet and collects information. By correlating the fingerprint of the certificate used with the Sonar SSL Certificates data set, we can find devices that are intentionally or unintentionally exposed to the web. In a recent scan we found more than 600.000 devices. We have analyzed the distribution of other static cryptographic secrets in use in embedded devices and have yet to find a certificate that is more frequently used than one by Ubiquiti Networks devices.
In the meantime the Censys Project by University of Michigan has launched. Censys is a scan-driven search engine that allows us to quickly find hosts that use the certificate. At the moment Censys reports that more than 1.100.000 devices are using this certificate (eb54c44a32a64497d8926ff87ba708f96fb0bff3).
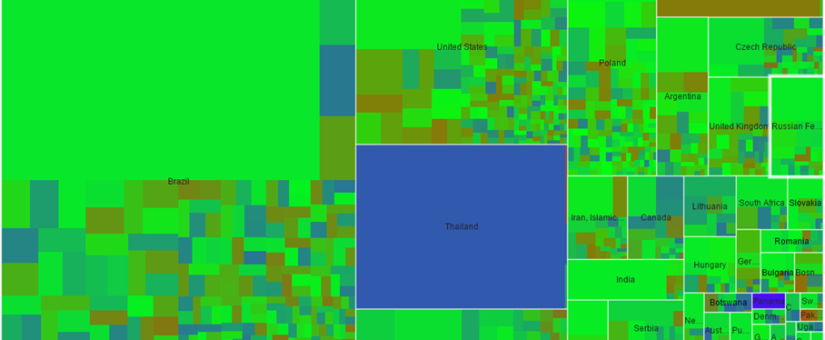
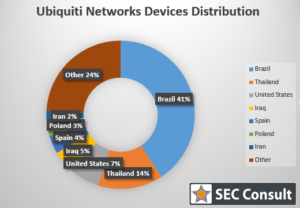
Most devices are located in Brazil (480.000), Thailand (170.000) and the United States (77.000), but deployments of significant size are found in the Iraq, Spain and Poland as well. We have created an interactive tree map that allows to explore the geographical distribution of affected hosts at a country and ISP/organization level. The tree map is based on the Scans.io data and covers less hosts than the data by Censys.